Unfortunately, it may possibly with MD5. In actual fact, back again in 2004, researchers managed to make two different inputs that gave a similar MD5 hash. This vulnerability is often exploited by terrible actors to sneak in malicious data.
Collision vulnerability. MD5 is at risk of collision assaults, wherever two unique inputs crank out a similar hash benefit. This flaw compromises the integrity of your hash functionality, allowing for attackers to substitute destructive facts devoid of detection.
Distribute the loveWith the internet becoming flooded using a myriad of freeware applications and software program, it’s challenging to differentiate among the authentic and the doubtless unsafe kinds. This is ...
This characteristic, often called the 'avalanche impact', improves the algorithm's sensitivity to details modifications. So, if you are sending your tune lyrics and in many cases one word alterations in transit, MD5 will capture it!
As an alternative to confirming that two sets of knowledge are similar by evaluating the raw facts, MD5 does this by creating a checksum on equally sets and after that evaluating the checksums to validate that they're the exact same.
Confined Digital Signatures: When protection was not the leading priority, MD5 algorithms created digital signatures. Having said that, as a result of its vulnerability to collision assaults, it's unsuited for sturdy digital signature programs.
As opposed to counting on here the MD5 algorithm, present day solutions like SHA-256 or BLAKE2 deliver stronger security and much better resistance to attacks, making certain the integrity and security of the programs and knowledge.
So how does an MD5 purpose function? In essence, you feed this tool knowledge—regardless of whether a doc, a video, a chunk of code, nearly anything—and in return, MD5 will crank out a singular and stuck-sized hash code. If even a single character is altered in that unique established of knowledge, it would develop a very different hash.
Hash Output: The moment all blocks are already processed, the final values in the state variables are concatenated to form the 128-little bit hash price. The output is often represented like a hexadecimal string.
Benjamin is a professional cybersecurity author whose get the job done explores topics for instance hacking, attack floor management, and cyberthreat defense of every kind. He is crafting professionally for more than 10 years and his get the job done has been highlighted in important media shops for instance HuffPost and YahooFinance. When he’s not around the clock, Benjamin enjoys looking at and writing fiction. Editorial Notice: Our articles supply instructional information to suit your needs.
MD5 in cryptography is usually a hash function that's notable as a result of many attributes, which include:
MD5 means “Concept-Digest Algorithm 5” and It is just a extensively-made use of cryptographic hash operate that converts any information into a hard and fast-dimension, 128-little bit hash. It had been invented by Ronald Rivest in 1991 and is usually accustomed to validate knowledge integrity.
Solutions Products With versatility and neutrality for the Main of our Okta and Auth0 Platforms, we make seamless and secure accessibility doable for your consumers, staff members, and associates.
This algorithm was produced by Ronald Rivest in 1991, and it is usually used in digital signatures, checksums, and various safety apps.
 Charlie Korsmo Then & Now!
Charlie Korsmo Then & Now!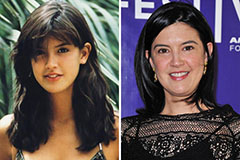 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Shannon Elizabeth Then & Now!
Shannon Elizabeth Then & Now! Bill Cosby Then & Now!
Bill Cosby Then & Now! Rossy de Palma Then & Now!
Rossy de Palma Then & Now!